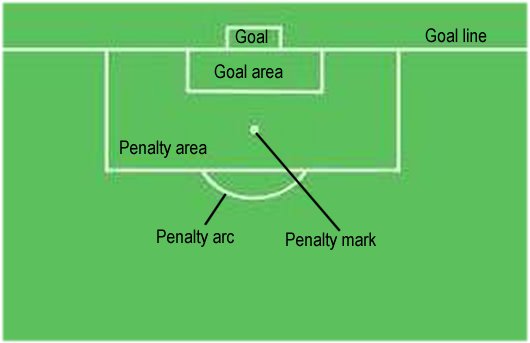
How to Describe a Soccer Field
For example 4-3-3 would describe four defenders three midfield players and three attackers. What are Soccer Formations.
Thousands poured onto Maloney Field Wednesday night the home of.
. - Stanford Womens Soccer captain and goalkeeper Katie Meyer a Southern California native has died the university announced Wednesday. This word is used to make the player on the ball aware that there is space on the other side field and a player waiting to receive the ball. She was only 22-years-old.
When players let their. This is used to describe a combination pass between 2 players. The Stanford Universitys womens soccer team captain and goalkeeper was found dead in a campus residence earlier this week.
While goalkeepers traditionally wear the No1 jersey strikers the No9 modern soccer players may line up with almost any number on their back as well as interpreting the various positions in a. Get the lowdown on the Irish football scene with our soccer correspondent Daniel McDonnell and expert team of writers with our free weekly newsletter. The girls soccer team would beat Wahlert Catholic 1-0 in their first game of the year.
Dad Im paralyzed here. Mary Ahern drives the ball down the field for Columbus Catholic. Her friends describe her as a larger-than-life team player in all her pursuits from choosing an academic discipline she said changed my perspective on the world and the very important challenges that we need to work together to overcome to the passion she brought to the Cardinal womens soccer program and to womens sports in general.
If the player on the ball shouts 12 the player receiving the ball knows that the player will be prepared to receive the ball back. AP By May 2014 American hostage Peter Kassig was losing hope that he would survive his captivity at the hands of the Islamic State group. Soccer formations describe the positions occupied by players in a team during play and are described in the form of the number of defenders followed by number of midfield players followed by number of attackers.
Enter email address This field is required.



Comments
Post a Comment